CrowdStrike Nightmare
Today I read that hospitals in Germany said they would cancel elective procedures; in Britain, doctors in the National Health Service were unable to gain access to their systems. Sky News, a major news channel in Britain, could not operate. At JPMorgan Chase there were delays in processing trades because bankers could not log into their work systems. At Disneyland Paris screens displaying wait times for rides went down. Alaska State Troopers told ABC News there have been 911 outages across the state.
I am truly sorry for all the CIO's, CTO's CISO's, and of course the technology teams that have had to address the CrowdStrike issue today. I know what you are facing, and I wish you a fast recovery and nothing but the best during this crisis.
Previously, I wrote about "black swan" technology risks, including technology supply chain risks, in Risky Business. Within any technology risk assessment program third-party software risk, especially software that could be "weaponized" against you, is critical to examine. Anti-virus software is always something that stands out. This risk is not new: In 2010 McAfee caused a global IT meltdown due to a faulty update. Fun fact: McAfee CTO at the time was George Kurtz, current CEO of CrowdStrike.
Anti-virus software generally works by using a signature file that contains patterns of known viruses and if a file is found that matches a pattern, the anti-virus software "neutralizes" that file. If the signature file could be corrupted, or poisoned in a way that targets system files, it's game over. Or in this case, if a bad kernel driver corrupts your system then it's also game over. Interestingly, CrowdStrike only uses a kernel-level driver for Microsoft Windows, not MacOS, or Linux. (Note to Microsoft: drivers which cause errors should be disabled automatically on next boot).
Then there are hidden costs in terms of system instability, CPU usage, power usage, heat, and sluggish system performance for all your users, all the time. Scanning for viruses, or validating system calls, consumes significant resources, slowing down the performance of the system it is meant to protect, and possibly destabilizing it.
All Anti-malware software, including solutions like CrowdStrike, faces numerous technical limitations. To name a few:
-
Zero-Day Threats and Fileless Malware: Traditional antivirus solutions rely on known signatures to detect malware. By definition "Zero-day" threats evade these signature-based detections because they haven't been included in the signature file yet. Virus definitions and heuristics need to be constantly updated to recognize the latest threats. This requires ongoing research and quick dissemination of updates to users. Fileless malware does not write any code to the disk, making it harder to detect since it operates entirely in memory. CrowdStrike attempts to mitigate many of these limitations through advanced techniques such as machine learning, threat intelligence integration, and behavioral analysis, but it is not immune to the inherent challenges.
-
Behavioral Detection Limitations: While behavioral detection can identify unknown threats by monitoring suspicious activities, it can sometimes result in higher false positive rates and may not detect all types of malware. False positives (legitimate files flagged as malicious) and false negatives (malicious files not detected) can both be problematic.
-
Evolving Evasion Techniques: Polymorphic malware can alter its code each time it infects a new system, making it difficult for signature-based detection methods to recognize the threat. Other techniques to evade detection, such as obfuscation, packing, and using anti-analysis methods to prevent their malware from being detected are always evolving and improving.
-
Encrypted and Compressed Files: Malware can be hidden in encrypted files or compressed files which are challenging to scan and analyze without using elevated system rights and impacting system performance.
-
Performance and Compatibility: Antivirus software must work seamlessly with various operating systems, applications, and other security tools. Incompatibilities can lead to instability, vulnerabilities, and/or reduced effectiveness.
Consider Application Whitelisting
What if I told you that you could reduce or eliminate:
- The cost of anti-malware software,
- The performance impact of anti-malware software,
- The stability impact of anti-malware software,
- The risk of zero-day, or obfuscated malware,
- The need to constantly update virus signature files on all you endpoints,
- False positives and false negatives,
- The risk of a poisoned signature file,
- and numerous other challenges?
Application whitelisting is a security practice that involves creating a list of approved applications that are permitted to run on a computer. Only the applications on the whitelist are allowed to be executed, while all other applications are blocked by default. This method prevents the execution of all unauthorized, and it's built into Microsoft Windows group policy.
Key points about application whitelisting:
-
Better Stability and Performance: It doesn't require a virus signature file, or a scanning engine to be running. No third-party kernel drivers. It doesn't destabilize a system or use excessive resources.
-
Improved Security Control: It protects against malware and unauthorized software by ensuring that only trusted applications can run. By restricting the execution of software to a predefined set of applications, organizations can significantly reduce the risk of zero-day attacks and improve their overall security posture.
-
Policy Enforcement: Whitelisting goes beyond just stopping malware - it enforces organizational policies regarding which software is permitted for use, aiding in compliance with regulatory requirements. Something anti-malware does not address.
-
Built-in to Microsoft Windows: Microsoft has built into its group policy a capability called "Software Restriction Policies" that only requires configuration and a management process to work. The management process involves continuously monitoring to detect and manage changes in the application landscape, ensuring that only verified updates and new applications are allowed. This effort can be funded from the savings of not buying, deploying, and supporting corporate anti-malware software.
Summary
Application whitelisting "flips the script". Instead of trying to detect and prevent malware, it only allows known, good applications to execute. Everything else is blocked by default.
Save money, improve your security, and avoid this:

A blue error screen, also known as the "Blue Screen of Death" inside Newark International Airport, after United Airlines and other airlines grounded flights due to a worldwide tech outage caused by an update to Crowdstrike's "Falcon Sensor" software. Newark, New Jersey, U.S., July 19, 2024. REUTERS/Bing Guan
References
- CrowdStrike: Statement on Falcon Content Update for Windows Hosts
- Flights and Businesses Are Struggling to Recover After Microsoft Windows Outage
- CrowdStrike outage sparks global chaos with airline, bank and other disruptions
- What is CrowdStrike, the company linked to the global outage?
- Wikipedia: 2024 CrowdStrike incident
- How to create an Application Whitelist Policy in Windows
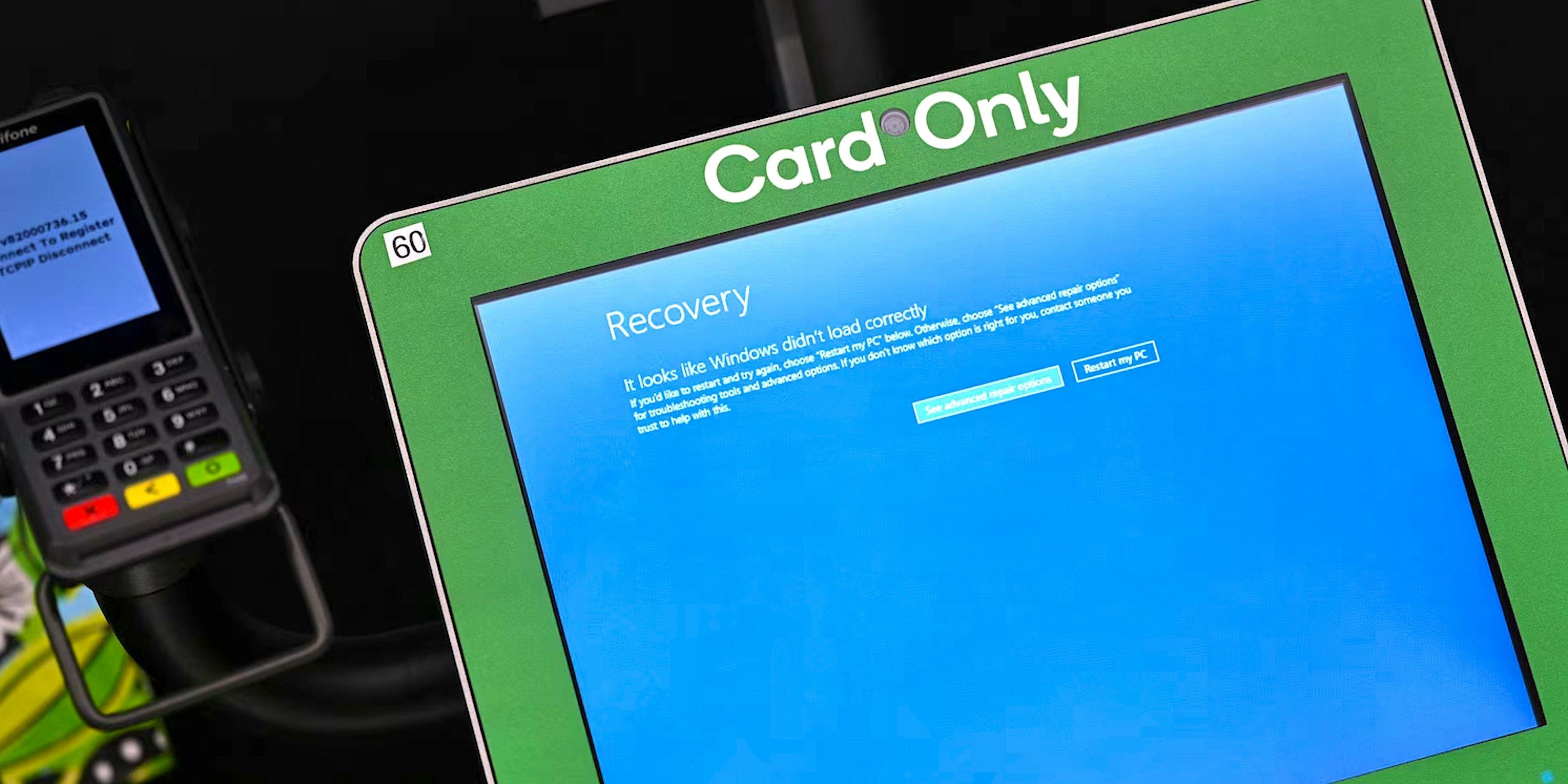
Image Credit: Crashed Supermarket Terminal in Sydney
A blue error screen on a self-checkout terminal of a supermarket in Sydney. July 19, 2024. Saeed Khan/AFP via Getty Images
